8 Essential Document Management Tips for 2025
In today's data-driven professional landscape, mastering your digital paperwork is a critical component of operational security, compliance, and overall productivity. Disorganized files, inconsistent naming conventions, and poor version control are not minor inconveniences; they can lead to costly errors, significant security vulnerabilities, and countless wasted hours searching for essential information. This guide offers a comprehensive roundup of actionable document management tips designed to transform your chaotic digital archives into a streamlined, secure, and highly efficient system.
We will explore practical, security-focused strategies that provide a clear roadmap for control and order. For professionals in fields like law, healthcare, and compliance, where accuracy and confidentiality are paramount, implementing these practices is non-negotiable. To truly tame the document beast and achieve secure and efficient workflows, it's essential to continuously assess and consider optimizing your document management workflow.
Furthermore, this article will highlight how integrating AI-powered solutions like Whisperit for dictation and editing can dramatically accelerate the initial stages of document creation. By leveraging such tools, you can significantly reduce the time spent on manual transcription and preliminary drafts, allowing you to focus on high-value analysis and strategic tasks. Prepare to reclaim your time and fortify your data with these essential strategies.
1. Implement a Standardized File Naming Convention
A standardized file naming convention is the foundational pillar of effective document management. It is a systematic, organization-wide set of rules for naming files to ensure every document is consistent, instantly recognizable, and easy to search for. This foundational strategy eliminates the chaos of ambiguous file names like "Draft" or "FinalReport_new," replacing them with a predictable and logical structure.

This approach involves defining a specific sequence of elements for your filenames. These elements often include the date, project or client code, document type, and version number. For example, a law firm might use a convention like [CaseNumber]_[DocumentType]_[DateYYYY-MM-DD]_[Version]. This simple change transforms a cluttered folder into a highly organized, searchable archive, making it one of the most impactful document management tips you can implement.
Why This Method is Crucial
Without a standard, employees are left to their own devices, resulting in inconsistent and often cryptic file names. This leads to wasted time searching for documents, accidental duplication, and a significantly higher risk of using outdated information. A clear naming convention creates a logical order that anyone in the organization can understand, improving workflow efficiency and reducing human error.
Major organizations recognize this value. Microsoft uses standardized naming for all internal projects, such as DEPT_ProjectName_DocumentType_YYYY-MM-DD_v#, to maintain clarity across global teams. Similarly, government agencies rely on strict naming protocols for compliance, auditing, and long-term records management as outlined by standards like ISO 15489.
Actionable Implementation Steps
To effectively deploy a naming convention, follow these practical steps:
- Start with a Pilot Group: Test and refine your proposed naming convention with a single department or team. This allows you to identify potential issues and gather feedback before a company-wide rollout.
- Create a Reference Guide: Develop a simple, one-page guide that clearly outlines the naming structure with specific examples for different document types (e.g., invoices, contracts, meeting notes).
- Automate Enforcement: Use features within your document management system or tools like SharePoint to create templates that automatically apply the correct naming convention.
- Integrate into Onboarding: Make the file naming guide a mandatory part of the onboarding process for all new employees to establish good habits from day one.
- Conduct Regular Audits: Periodically review file storage to ensure compliance and correct any deviations. This reinforces the importance of the standard and keeps the system clean.
2. Establish a Hierarchical Folder Structure
A hierarchical folder structure is a logical system of nested folders and subfolders that mirrors your organization's workflow, departments, or project framework. It creates a clear, intuitive pathway for document storage and retrieval, ensuring users can instinctively find and file information in the correct location without second-guessing. This organizational clarity prevents digital clutter and makes your file system navigable for everyone.
This logical hierarchy is one of the most fundamental document management tips, transforming a chaotic digital space into a streamlined, predictable environment. The infographic below illustrates a common and effective three-level structure.
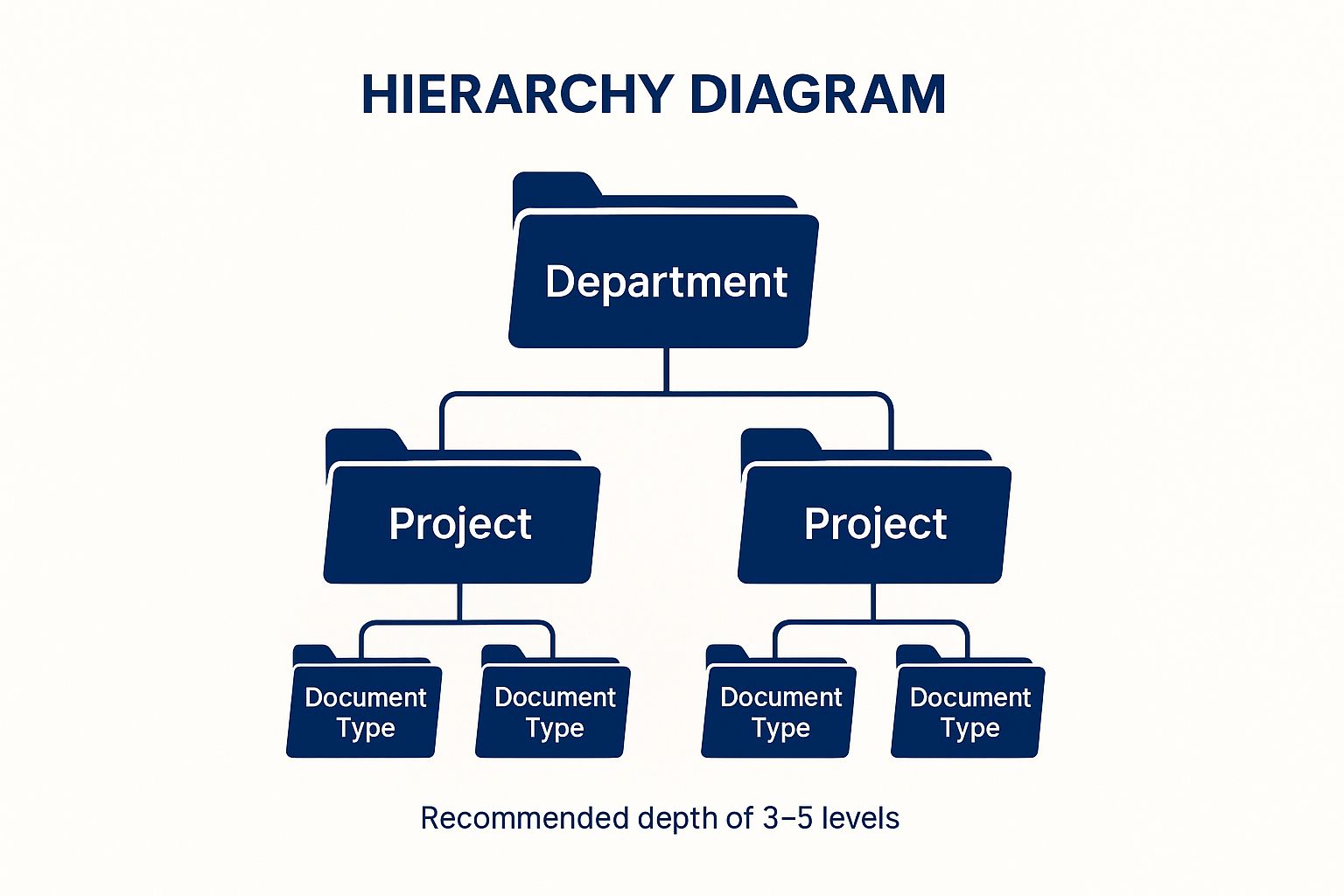
This visual shows how a top-level category like "Department" branches into more specific "Project" folders, which in turn contain categorized "Document Type" subfolders, creating an intuitive path to any file.
Why This Method is Crucial
Without a planned folder hierarchy, teams often create redundant, disorganized folders, leading to a digital "wild west" where documents are easily lost. A well-designed structure provides a single source of truth, drastically reducing search times and the risk of using incorrect or outdated files. It also simplifies access control, as permissions can be set at higher folder levels and inherited by the subfolders within.
Major consulting firms like Deloitte use a global folder structure organized by client, service line, and engagement year to maintain consistency. Likewise, construction companies often structure folders by project, phase (e.g., Bidding, Design, Construction), and document type (e.g., Blueprints, RFIs, Contracts), ensuring critical documents are always accessible.
Actionable Implementation Steps
To build a robust and scalable folder hierarchy, follow these practical steps:
- Limit Folder Depth: Keep your structure from becoming too complex. A good rule of thumb is to limit folder depth to three to five levels to avoid excessive clicking and user frustration.
- Start Broad, Get Specific: Use broad, stable categories for your top-level folders (e.g., Departments, Clients, Fiscal Years) and become more granular as you go deeper.
- Use Numbered Prefixes: To control the order in which folders appear, use numbered prefixes (e.g.,
01_Marketing,02_Sales,03_Operations). This is especially useful for process-driven workflows. - Create a Reference Map: Develop a simple visual map or guide of your folder structure and share it with all team members. For specialized fields like law, it's essential to organize legal case files with precision and consistency. You can learn more about how to organize legal case files on whisperit.ai.
- Regularly Prune and Audit: Schedule quarterly or bi-annual reviews to archive old projects and delete empty or redundant folders. This maintenance keeps the structure clean and efficient.
3. Implement Version Control and Document Lifecycle Management
Beyond just naming files, effective document management tips must address how documents evolve. Version control and document lifecycle management are intertwined processes for tracking changes and managing a document from its creation to its archival or disposal. This ensures every team member works with the most current, approved version while maintaining a complete historical record for compliance and auditing.
This system prevents the costly error of using outdated information, a critical concern in regulated industries. It involves assigning clear version numbers (e.g., v1.0, v1.1, v2.0) and managing the document’s status, such as Draft, In Review, Approved, or Archived. It defines a clear path for a document’s journey, ensuring it is handled correctly at every stage.
Why This Method is Crucial
Without formal version and lifecycle control, chaos reigns. Multiple "final" versions of a document can float around, leading to confusion, duplicated effort, and significant compliance risks. This framework establishes a single source of truth, guaranteeing that decisions are based on the correct data. To delve deeper into maintaining the integrity and accessibility of your documents throughout their lifecycle, consider mastering document control procedures for a structured approach.
This isn't just theory; it's a standard practice in high-stakes environments. For instance, pharmaceutical companies like Pfizer rely on stringent version control for all drug development documentation to meet FDA regulations. Similarly, engineering firms use it to manage technical drawings and specifications, where a minor error from an old version could have catastrophic consequences. This structured oversight is fundamental to modern information governance.
Actionable Implementation Steps
To deploy a robust version control and lifecycle system, follow these steps:
- Establish Clear Versioning Rules: Define when a change constitutes a minor edit (v1.1) versus a major revision (v2.0). Document this in a clear policy and train your team on the distinction.
- Implement Approval Workflows: Use your document management system to create automated workflows that require key stakeholders to review and approve documents before they are finalized. This is a core component of a strong document review process.
- Utilize Check-In/Check-Out Features: Train users on check-in/check-out procedures available in most document platforms. This locks a document during editing, preventing simultaneous, conflicting changes.
- Define Retention and Purge Policies: Create a schedule for how long different document types and their previous versions must be kept. Regularly audit and purge outdated documents according to this policy to reduce clutter and mitigate risk.
- Automate Version Numbering: Configure your system to automatically assign the next version number upon saving or approval. This reduces human error and ensures the protocol is consistently followed.
4. Utilize Metadata and Tagging Systems
Metadata and tagging systems are the digital equivalent of a detailed index card for every document, providing rich, searchable context that goes far beyond a filename. This method involves attaching descriptive information, or "data about data," to files, such as author, creation date, project code, status, or custom keywords. This strategy transforms your document repository from a simple collection of files into an intelligent, relational database.
While a strong naming convention tells you what a file is, metadata tells you everything else about it. For example, a legal contract's metadata could include the client name, matter number, contract expiration date, and review status. This allows professionals to instantly filter and find all documents expiring in the next 30 days or all active contracts for a specific client, a task impossible with filenames alone. This makes it one of the most powerful document management tips for complex environments.
Why This Method is Crucial
Relying solely on folder structures and file names creates information silos and limits searchability. Metadata breaks down these barriers, enabling dynamic, multi-faceted searches that mirror how people actually think and work. It significantly reduces search time, prevents the loss of critical context, and enhances compliance by making it easier to manage document lifecycles based on properties like "record type" or "retention date."
This practice is standard in information-heavy industries. News organizations like Reuters use extensive metadata to categorize articles and images by topic, location, and event, enabling rapid content retrieval and syndication. Similarly, marketing agencies tag creative assets with campaign, client, and usage rights information, preventing costly compliance violations.
Actionable Implementation Steps
To effectively integrate metadata and tagging, follow these practical steps:
- Define Core Metadata Fields: Identify a mandatory set of metadata for all documents (e.g., Document Type, Author, Status). Use controlled vocabularies or dropdown menus instead of free-text fields to ensure consistency.
- Create Metadata Templates: In your document management system, configure templates for common document types (e.g., invoices, reports, contracts) that automatically prompt users for the relevant metadata upon upload.
- Leverage Automation: Use tools that can automatically extract metadata from documents, such as the creation date, author, or even keywords from the text itself. AI-powered tools can further enhance this by suggesting relevant tags based on content analysis.
- Provide Contextual Training: Train employees not just on how to add metadata, but why it is valuable. Show them how it improves their own search efficiency and contributes to organizational intelligence.
- Integrate with Workflows: Link metadata to business processes. For example, changing a document’s status tag from "Draft" to "Approved" could automatically trigger a notification to the next person in the workflow.
5. Implement Regular Backup and Disaster Recovery Procedures
A robust backup and disaster recovery (DR) plan is the ultimate safety net for your digital assets, safeguarding them against system failures, data corruption, natural disasters, and cyber attacks like ransomware. This strategy involves systematically creating copies of critical documents and establishing clear procedures to restore access swiftly after an incident. It moves an organization from a reactive panic to a proactive, controlled response, ensuring business continuity and data integrity.

The core idea is to eliminate single points of failure. By storing multiple copies of your data across different media and locations, you create redundancy. If your primary server fails or an office is inaccessible, a well-designed DR plan allows you to retrieve your documents from a secure backup and resume operations with minimal downtime, making it one of the most essential document management tips for modern resilience.
Why This Method is Crucial
Without a formal backup and recovery strategy, a single event can be catastrophic, leading to permanent data loss, severe financial penalties, and irreversible reputational damage. This is especially critical in regulated industries where data availability is a compliance mandate. A documented DR plan ensures that everyone knows their role during a crisis, preventing confusion and enabling a rapid, organized recovery.
Industries with high stakes rely on these procedures. Hospitals maintain redundant, offsite backups of patient records to ensure uninterrupted care, even during a system outage. Similarly, financial institutions use geographically distributed backups to comply with strict regulatory requirements and protect client assets. Law firms also implement comprehensive backup strategies to uphold client confidentiality and prevent the loss of irreplaceable case files.
Actionable Implementation Steps
To build an effective backup and disaster recovery plan, follow these practical steps:
- Follow the 3-2-1 Backup Rule: This industry best practice, popularized by IT disaster recovery specialists, is a simple yet powerful framework. Maintain at least three copies of your data on two different types of storage media, with one copy stored offsite.
- Test Your Backups Regularly: A backup is only useful if it works. Schedule and perform quarterly restoration tests to verify data integrity and ensure your recovery process is effective. This identifies issues before a real disaster strikes.
- Document and Train: Create a detailed disaster recovery plan that outlines step-by-step procedures for different scenarios. Train key personnel on their specific roles and responsibilities to ensure a coordinated response.
- Leverage Cloud Backup Services: Utilize cloud services like Backblaze or Carbonite for automated, secure offsite storage. These solutions simplify the process and often include features like versioning and continuous data protection.
- Implement Proactive Monitoring: Set up automated alerts that notify your IT team immediately of any backup failures or anomalies. This allows for quick troubleshooting and ensures your backup system remains reliable.
6. Establish Clear Access Controls and Security Permissions
Establishing clear access controls and security permissions is a non-negotiable component of modern document management. It involves creating and enforcing a systematic set of rules that dictate who can view, edit, create, or delete documents within your organization's systems. This security layer ensures that sensitive information remains confidential and is only accessible to authorized individuals, protecting against both internal and external threats.
This process relies on mechanisms like user authentication, role-based access control (RBAC), and granular, document-level permissions. For instance, a healthcare organization uses HIPAA-compliant controls to ensure only treating physicians can access specific patient records, while a financial firm restricts access to client data to only the assigned relationship managers. These controls are foundational for maintaining data integrity, compliance, and operational security.
Why This Method is Crucial
Without robust access controls, sensitive data like financial records, intellectual property, or personal information is left vulnerable. This oversight can lead to data breaches, compliance violations, and significant reputational damage. By implementing a "principle of least privilege," where users are only granted the minimum access necessary to perform their jobs, you dramatically reduce the attack surface and minimize the risk of accidental or malicious data exposure.
This principle is a core tenet of major information security frameworks. Compliance standards like ISO 27001 and NIST explicitly require organizations to define and manage access rights. Defense contractors and government agencies use multi-level security clearances as a form of access control to protect classified information, demonstrating its critical importance in high-stakes environments. You can learn more about how these strategies protect your most vital assets by reading about document management security.
Actionable Implementation Steps
To effectively implement access controls and permissions, follow these practical steps:
- Audit and Define Roles: Begin by mapping out all job roles within your organization and defining the specific data access each role requires. Use this map to create role-based access groups.
- Implement a "Least Privilege" Policy: Start by assigning a baseline, "no access" permission level to all users. Then, grant specific permissions based on the defined roles rather than starting with broad access and trying to restrict it later.
- Automate Employee Lifecycle Changes: Integrate your document management system with your HR system to automatically grant access to new hires and, more importantly, revoke all access immediately upon an employee's termination.
- Conduct Regular Access Reviews: Schedule quarterly or semi-annual audits of user permissions. This ensures that access rights remain aligned with current job responsibilities and removes any permissions that are no longer necessary.
- Establish a Formal Request Process: Create a clear, documented procedure for employees to request access to specific documents or systems, including who needs to approve the request.
7. Conduct Regular Document Audits and Cleanup
Regular document audits and cleanup are essential maintenance activities for a healthy document management system. This practice involves systematically reviewing your entire document repository to identify and deal with redundant, obsolete, or trivial (ROT) files. By actively removing or archiving unnecessary documents, you ensure your system remains efficient, secure, and compliant.
This proactive approach prevents digital clutter from accumulating, which can slow down system performance and make critical information difficult to find. Instead of waiting for a storage crisis or a compliance issue, regular audits maintain a clean and optimized environment, turning your digital storage from a cluttered attic into a well-organized library.
Why This Method is Crucial
Without periodic audits, document repositories inevitably suffer from bloat. This leads to increased storage costs, slower search performance, and a higher risk of employees using outdated or incorrect information. Furthermore, retaining documents beyond their required retention period can create significant legal and compliance liabilities, especially in regulated industries like healthcare and law.
This practice is a core component of professional records management and IT governance frameworks. For example, legal firms conduct annual audits to ensure they comply with client confidentiality agreements and data retention policies. Similarly, IT departments regularly audit technical documentation to purge obsolete procedures and prevent security vulnerabilities. These audits are crucial document management tips for maintaining data integrity and operational discipline.
Actionable Implementation Steps
To execute a successful document audit and cleanup, follow these steps:
- Prioritize for Impact: Begin your audit by targeting the oldest and largest files first. This approach delivers the most significant impact on storage space and system performance with minimal initial effort.
- Leverage Automation: Use your document management system’s built-in tools or specialized software to automatically identify duplicate files, documents that haven't been accessed in years, and other ROT data.
- Establish a Quarantine Zone: Before permanently deleting files, move them to a temporary "quarantine" or "to-be-deleted" folder. This provides a safety net, allowing document owners to review and retrieve any files that were flagged for deletion by mistake.
- Involve Document Owners: Engage the original creators or department heads in the review process. They have the best context to determine whether a document is still valuable or can be safely archived or deleted.
- Document Your Process: Keep a detailed log of the audit process, including what was reviewed, what actions were taken, and who approved the changes. This creates a defensible audit trail and helps refine your document workflow management for future cleanups.
8. Provide Comprehensive User Training and Support
A sophisticated document management system is only as effective as the people using it. Providing comprehensive user training and support ensures that every employee understands the tools, procedures, and security protocols required for success. This involves more than a one-time onboarding session; it is an ongoing commitment to educating users on everything from file naming conventions to advanced system features and security best practices.
This process equips staff with the knowledge to use the system efficiently, consistently, and securely. It bridges the gap between technology implementation and user adoption, transforming a powerful tool into an integrated part of the daily workflow. Without proper training, even the best systems suffer from low adoption rates, inconsistent usage, and increased security vulnerabilities, negating the investment.
Why This Method is Crucial
Investing in a document management platform without allocating resources for training is a recipe for failure. Untrained users will inevitably revert to old, inefficient habits, create organizational chaos, and expose the company to significant risks. To ensure your document management system remains secure, provide comprehensive user training that includes awareness about social engineering tactics. Proper education empowers employees, reduces support requests, and maximizes the return on your technology investment.
Leading organizations prioritize this. For example, major hospitals conduct rigorous training for all medical staff on their electronic health record (EHR) systems to ensure patient data is managed accurately and securely, in compliance with HIPAA. Similarly, professional services firms like Accenture provide extensive SharePoint training so consultants can collaborate effectively and manage client documents according to strict standards.
Actionable Implementation Steps
To build a successful training and support program, consider these practical steps:
- Create Bite-Sized Modules: Develop short, focused training videos or guides that users can consume quickly. This is more effective for retention than long, monolithic training sessions.
- Use Role-Relevant Scenarios: Tailor training materials to the specific needs and workflows of different departments. A legal team needs different examples than a marketing team.
- Establish "Super-Users": Identify and train power users within each department to act as the first line of peer support, answering common questions and promoting best practices.
- Provide Just-in-Time Resources: Embed help guides, FAQs, and short tutorials directly within your document management system so users can get answers without leaving their workflow. Learn more about how to get started with streamlined workflows to enhance user adoption.
- Measure Training Effectiveness: Track usage metrics, conduct surveys, and gather user feedback to identify areas where additional training is needed and to measure the program's impact on efficiency.
Document Management Tips Comparison
| Method | Implementation Complexity 🔄 | Resource Requirements ⚡ | Expected Outcomes 📊 | Ideal Use Cases | Key Advantages ⭐ |
|---|---|---|---|---|---|
| Implement a Standardized File Naming Convention | Medium - requires initial setup and training | Low - mostly policy and enforcement | Improved searchability, reduced duplicates | Organizations needing consistent document IDs | Boosts collaboration, automated sorting |
| Establish a Hierarchical Folder Structure | Medium - needs design and ongoing upkeep | Low to Medium - depends on scale | Intuitive navigation, scalable document storage | Businesses with complex or growing document sets | Supports backup, reduces misfiling |
| Implement Version Control and Document Lifecycle Management | High - involves training and system setup | Medium - version storage overhead | Clear version tracking, auditability | Regulated industries, technical documentation | Prevents data loss, ensures compliance |
| Utilize Metadata and Tagging Systems | Medium to High - requires consistent data entry | Medium - metadata tools and governance | Enhanced search/filtering, richer context | Large, diverse document collections | Enables automated processing, improves discoverability |
| Implement Regular Backup and Disaster Recovery Procedures | High - requires infrastructure and planning | High - backup systems and maintenance | Data protection, business continuity | Critical data environments (healthcare, finance) | Guards against data loss, supports compliance |
| Establish Clear Access Controls and Security Permissions | High - ongoing maintenance and complex setup | Medium - security tools and audits | Protected sensitive info, tracked access | Organizations with confidential data | Reduces breach risk, enables secure collaboration |
| Conduct Regular Document Audits and Cleanup | Medium to High - time-intensive review cycles | Medium - audit tools and manpower | Reduced clutter, better compliance | Mature repositories needing optimization | Improves performance, reduces storage costs |
| Provide Comprehensive User Training and Support | Medium - ongoing program development | Medium - training materials and staff | Higher adoption, fewer errors, greater productivity | All organizations implementing new systems | Builds user confidence, lowers support load |
From Chaos to Control: Finalizing Your Document Strategy
Navigating the complex landscape of modern information requires more than just good intentions; it demands a strategic, systematic approach. We have journeyed through a comprehensive set of eight foundational document management tips, moving from the granular details of file naming conventions to the high-level strategy of regular security audits. Each principle, whether it's establishing a logical folder hierarchy, implementing rigorous version control, or leveraging metadata for enhanced searchability, serves as a critical pillar in constructing a secure and efficient information ecosystem.
The transition from digital chaos to structured control is not an overnight event. It is a deliberate process built on consistency, clarity, and commitment. The strategies outlined are not isolated tactics but interconnected components of a larger information governance framework. A standardized naming convention is exponentially more powerful when paired with a hierarchical folder structure. Similarly, clear access controls are fortified by regular document audits that ensure those controls remain effective and relevant over time.
Synthesizing Strategy into Action
To truly transform your organization's approach, it's crucial to see these tips not as a checklist to be completed, but as a continuous cycle of improvement. The core takeaways from our discussion can be distilled into three key themes:
- Structure is Paramount: Without a foundational structure for how documents are named, stored, and organized, even the most advanced software will fail to deliver its full potential. This is your blueprint for efficiency.
- Security is a Process, Not a Product: Implementing access controls and backup procedures is the first step. The real work lies in the ongoing processes of auditing, training, and adapting to new threats and compliance requirements. Security must be an active, not a passive, consideration.
- Technology is a Multiplier: The right tools do not replace strategy, they amplify it. When your foundational practices are sound, technologies like AI-powered dictation and editing can dramatically accelerate workflows, reduce human error, and ensure compliance within your established framework.
Your Path Forward: From Theory to Implementation
Mastering these concepts is no longer a luxury for specialized roles; it is a fundamental necessity for any professional dealing with sensitive information, from legal practitioners drafting contracts to healthcare providers managing patient records. The value extends far beyond simple organization. It directly impacts productivity, mitigates legal and financial risk, enhances data security, and ensures regulatory compliance. A robust document management system is the backbone of operational excellence and a key differentiator in a competitive landscape.
Your immediate next steps should be both strategic and manageable. Do not attempt to overhaul your entire system at once. Instead, identify the area of greatest friction or highest risk within your current workflow.
- Start with a Pilot Project: Choose a single department or a specific type of document (e.g., client intake forms, case files) to apply these principles.
- Focus on Foundational Wins: Begin with implementing a standardized file naming convention and a clear folder structure. These are high-impact changes that create immediate clarity.
- Build Momentum and Foster Culture: Use the success of your pilot project to build a case for broader implementation. Provide comprehensive training and emphasize that effective document management is a shared responsibility, crucial for protecting the organization and its clients.
Ultimately, the goal is to cultivate a culture where thoughtful information handling is second nature. By embracing these document management tips, you are not just cleaning up digital files; you are building a resilient, efficient, and secure foundation for your organization's future success.
Ready to supercharge your document creation process within a secure, compliant framework? Discover how Whisperit leverages cutting-edge AI for dictation and editing, allowing professionals to produce accurate, detailed documents in a fraction of the time. Integrate a powerful efficiency tool into your newly optimized workflow by visiting Whisperit today.