Your Ultimate Guide to a HIPAA Compliant Document Management System
Think of a HIPAA compliant document management system as a digital fortress, purpose-built from the ground up to store, manage, and share Protected Health Information (PHI) according to the government's strict rules. It’s not just about storage; it's a complete ecosystem of security features like encryption, access controls, and detailed audit trails, all working together to keep patient data private and secure. For any modern healthcare organization, it's an absolutely essential tool.
What Is a HIPAA Compliant Document Management System?
Let's use an analogy. Imagine a high-security bank vault. It's not just a room with a strong lock; it has layers upon layers of protection. A HIPAA compliant document management system (DMS) functions in the exact same way for your digital patient files, going miles beyond what a basic service like Dropbox or Google Drive can offer.
Here’s how it breaks down:
- The vault's reinforced steel walls are like encryption. This feature scrambles data, making it completely unreadable to anyone without the right key, both when it's sitting on a server (at rest) and when it's being sent (in transit).
- The biometric scanners that grant entry only to specific, authorized personnel are just like access controls. These digital controls ensure that only the right people can view, edit, or share certain documents, which is crucial for upholding HIPAA's "minimum necessary" principle.
- The 24/7 video surveillance that records every single person who enters and leaves is the system’s audit trail. This creates a permanent, unchangeable log of every action taken—who accessed what file, when they did it, and what they did with it.
Trying to manage PHI with a standard file-sharing service is the digital equivalent of leaving a stack of patient charts on a public park bench. The risk is enormous, leading not just to massive fines but also to a loss of patient trust that can be impossible to get back.
The Core Pillars of a Compliant System
It's no surprise that the demand for these specialized systems is skyrocketing. The healthcare industry is the biggest player in the global document management market, accounting for over 23% of the total share. This growth is a direct result of the shift to electronic health records (EHR) and the push for paperless offices, all of which fall under HIPAA's watchful eye.
To be truly effective, a DMS must stand on several core pillars. Think of these as the non-negotiable foundations for protecting sensitive health information. Getting a handle on these components is the first step toward choosing the right system for your practice.
For a comprehensive list of every requirement, you can explore our complete HIPAA compliance requirements checklist.
Here's a quick summary of the essential components that make a document management system truly HIPAA compliant.
Core Pillars of a HIPAA Compliant DMS
| Pillar | What It Means in Practice | Its Role in HIPAA Compliance |
|---|---|---|
| Access Control | Implementing role-based permissions, multi-factor authentication, and automatic logoffs. | Ensures only authorized staff can access PHI, directly addressing a core Security Rule requirement. |
| Audit Trails | Creating detailed, immutable logs of all user activity, including views, edits, and shares. | Provides the necessary records for security audits and breach investigations, ensuring accountability. |
| Data Encryption | Securing data with strong encryption algorithms, both when stored on servers and during transmission. | Renders PHI unusable if intercepted or stolen, serving as a critical technical safeguard. |
| Secure Backup | Maintaining encrypted, recoverable copies of all data in a separate, secure location. | Guarantees data integrity and availability in case of a system failure or disaster, as mandated by HIPAA. |
| Business Associate Agreement (BAA) | A legal contract where the DMS vendor agrees to protect PHI according to HIPAA rules. | Establishes legal liability and confirms the vendor’s commitment to safeguarding your data. |
Each pillar plays a distinct but interconnected role. Without all of them working in concert, you leave gaps in your security—and that’s a risk no healthcare provider can afford to take.
Decoding the HIPAA Security Rule for Digital Documents

The HIPAA Security Rule can feel like a dense, intimidating legal document. But when you boil it down, its core mission is simple and practical: to protect sensitive patient information in a digital world. When you bring a hipaa compliant document management system into your workflow, you’re not just buying a piece of software. You're adopting a tool specifically built to turn those complex rules into real-world, everyday actions.
I like to think of the Security Rule as a three-legged stool. For that stool to be stable enough to support your compliance obligations, all three legs—Administrative, Physical, and Technical Safeguards—must be equally strong. If one leg is weak or missing, the whole thing comes crashing down.
Administrative Safeguards: The Human Element
This first leg is all about your people, policies, and procedures. It’s the "who" and "how" of your security strategy, defining how you expect your team to handle electronic Protected Health Information (ePHI). It’s one thing to have a policy written down in a binder, but it’s another thing entirely to enforce it consistently.
This is where a document management system provides the framework to make your policies real.
Key administrative actions include:
- Appointing a Security Official: You need to designate one person who is ultimately responsible for developing, implementing, and overseeing your security policies.
- Workforce Training: It's critical to regularly train your staff on security protocols. This means teaching them how to spot phishing emails and follow the correct procedures for handling patient records within the document system.
- Conducting a Risk Analysis: You have to perform regular assessments to find potential weak spots where the confidentiality, integrity, or availability of ePHI could be compromised.
- Creating a Contingency Plan: What happens if there's an emergency or system failure? A solid plan, including data backup and disaster recovery procedures managed through your document system, is essential.
A well-implemented document management system becomes the backbone of your administrative strategy. It gives you the tools to enforce the very policies you create, turning abstract rules into concrete, trackable actions that protect your practice and your patients.
Physical Safeguards: Securing the Hardware
The second leg of the stool, Physical Safeguards, is about protecting the actual hardware where ePHI lives. This includes everything from servers and desktop computers to tablets and the buildings they're in. Think of it as the modern version of putting a sturdy lock on the door to the paper file room.
This seems obvious for servers sitting in your own office, but it's just as crucial when you use cloud-based systems. When you partner with a vendor like Whisperit for a hipaa compliant document management system, you're relying on them to handle the physical security of the servers in their highly protected data centers.
These safeguards cover things like:
- Facility Access Controls: Limiting who can physically get into data centers and server rooms. This means locks, security guards, surveillance—the works.
- Workstation Security: Implementing policies for the computers and devices that access ePHI. This includes simple but effective measures, like making sure screens aren't visible to the public and that devices automatically log off after being idle.
- Device and Media Controls: Creating strict procedures for how you handle and securely dispose of old hard drives, USB sticks, or any other electronic media that has ever held ePHI.
Technical Safeguards: The Digital Locks
Finally, we have the Technical Safeguards. These are the digital locks and keys—the technology and related policies you use to protect ePHI and control who can access it. This is where a specialized document management system really proves its worth, as these features are woven into its very DNA.
Key technical components include:
- Access Control: The system must let you give each user a unique login and then restrict their access based on their job role. This enforces the "minimum necessary" rule, ensuring people only see the information they absolutely need to do their jobs.
- Audit Controls: Your system needs to keep a detailed, unchangeable log of all activity. Every time a document is viewed, downloaded, or edited, it should be tracked. This creates a clear trail for accountability.
- Integrity Controls: You need to be confident that ePHI hasn't been improperly changed or deleted. A good system has mechanisms that prevent unauthorized alterations to documents.
- Transmission Security: When data is sent across a network—for instance, when sharing a file—the system must use powerful encryption to shield it from being intercepted.
These three safeguards are designed to work in concert, creating a powerful defense for patient data. Mastering them is the key to compliance. For anyone looking to sharpen their processes, it’s always a good idea to review foundational document management best practices that reinforce these principles. To see how vendors commit to this on their end, you can review a typical privacy policy for document services.
Must-Have Features in a HIPAA Compliant System

When you start looking at document management vendors, it’s easy to get lost in a sea of features and promises. But when HIPAA compliance is at stake, not all bells and whistles are created equal. A genuinely hipaa compliant document management system isn’t just about storage; it’s defined by a handful of non-negotiable features that directly answer the demands of the Security Rule.
Think of it like outfitting a ship for a long voyage. You wouldn't set sail without life rafts, navigation tools, and a solid hull. In the same way, you can't manage Protected Health Information (PHI) without the right digital protections. Each one has a specific job to do in keeping your data safe from prying eyes, corruption, or outright loss.
Granular Access Controls
First up, and arguably the most foundational feature, is granular access control. This is your system’s digital bouncer, checking IDs at every door and only letting authorized people through. It's not enough to just have a single password for your team; a compliant system has to let you enforce HIPAA’s "Minimum Necessary" standard with surgical precision.
This means you can dictate exactly who sees a document and what they can do with it. For example, a billing clerk might need to view invoices but should be blocked from seeing a patient's clinical notes. A doctor, on the other hand, needs full access to edit their own patients' charts but shouldn't be able to browse records from another department. While this level of control is essential in healthcare, the same principles apply in any field where confidentiality is paramount. In fact, many professionals find that looking at guides on law firm document management offers helpful parallels for protecting sensitive information.
Immutable Audit Trails
Next, your system must have immutable audit trails. This is your black box—the indisputable log of every single action that happens inside the system. Just like a flight recorder, an audit trail tracks who accessed what, when they did it, and what they did (view, edit, download, share, etc.).
These logs are your cornerstone for accountability. If there's a security incident or you're facing a routine audit, these trails offer a clear, chronological story that can prove you've done your due diligence or help you pinpoint the source of a breach. An audit log that can be edited is completely worthless; it must be permanent.
Robust Data Encryption
Encryption is the bedrock of modern digital security. It’s the art of scrambling data into unreadable code that can only be unlocked with a specific key. For a hipaa compliant document management system, encryption isn't just a nice-to-have—it's mandatory for data in two states:
- Data at Rest: This is PHI sitting on a server or a hard drive. If a physical server gets stolen, encryption ensures the thief is left with a useless jumble of code.
- Data in Transit: This is PHI moving across a network, like when you email a file to a specialist or when data travels from your computer to the cloud. Encryption acts like a digital armored truck, protecting it from being intercepted along the way.
Knowing how to encrypt and share files securely is a foundational skill for anyone handling sensitive information in a HIPAA-regulated environment.
Secure Backup and Disaster Recovery
So, what happens if your main system goes down? A server could fail, a natural disaster could strike, or a ransomware attack could lock you out. The HIPAA Security Rule demands that you have a contingency plan. A compliant system must provide automated, secure backups and have a solid disaster recovery protocol.
This means an exact, up-to-date copy of all your PHI is stored safely in a different, secure location. This redundancy is what allows you to get back up and running quickly after an incident, ensuring you maintain the data availability and integrity the law requires.
The Essential Business Associate Agreement
Finally, we come to what might be the most critical piece of the legal puzzle: the Business Associate Agreement (BAA). This is a formal, legally binding contract that makes your vendor (the "business associate") just as responsible for protecting your PHI as you are.
If you share PHI with any outside service—including your document management provider—without a signed BAA in place, you are committing a direct HIPAA violation. This document is your proof that the vendor understands and accepts their legal duties. Never, ever work with a vendor who won’t or can’t sign one. It's a massive red flag.
Implementing Your New Document Management System
Picking the right vendor feels like a huge win, but let's be honest—the real work in becoming compliant starts now. Rolling out a HIPAA compliant document management system is much more than a simple software install; it's a strategic project. This is the point where your carefully crafted policies and the system's powerful technology finally come together to create a fortress for Protected Health Information (PHI).
Think of it like adding a state-of-the-art secure wing to a hospital. You wouldn't just install some fancy locks and cameras and walk away. You'd need a detailed blueprint, a clear construction plan, and a team that knows exactly how to operate the new security features. The same logic applies here. A successful DMS implementation demands meticulous planning, from the first assessment to the day-to-day management that follows.
This process ensures your system is set up correctly right from the start, closing potential security gaps and empowering your team to use it effectively.
Conduct a Thorough Risk Assessment
Before you even think about moving a single file, you have to start with a risk assessment. This isn't just a good idea; it's a foundational requirement under HIPAA. The goal is to systematically look at your entire workflow and identify any potential threats or vulnerabilities to the PHI you manage. Where could a breach realistically happen? What are your weakest links, both in terms of technology and human error?
Answering these questions gives you a brutally honest map of your security landscape. The insights you gain will become the blueprint for configuring your new document management system, allowing you to point its security features directly at your organization’s unique risks.
The difference between sticking with old manual processes and upgrading to an automated, HIPAA-compliant system is night and day. This infographic paints a very clear picture.
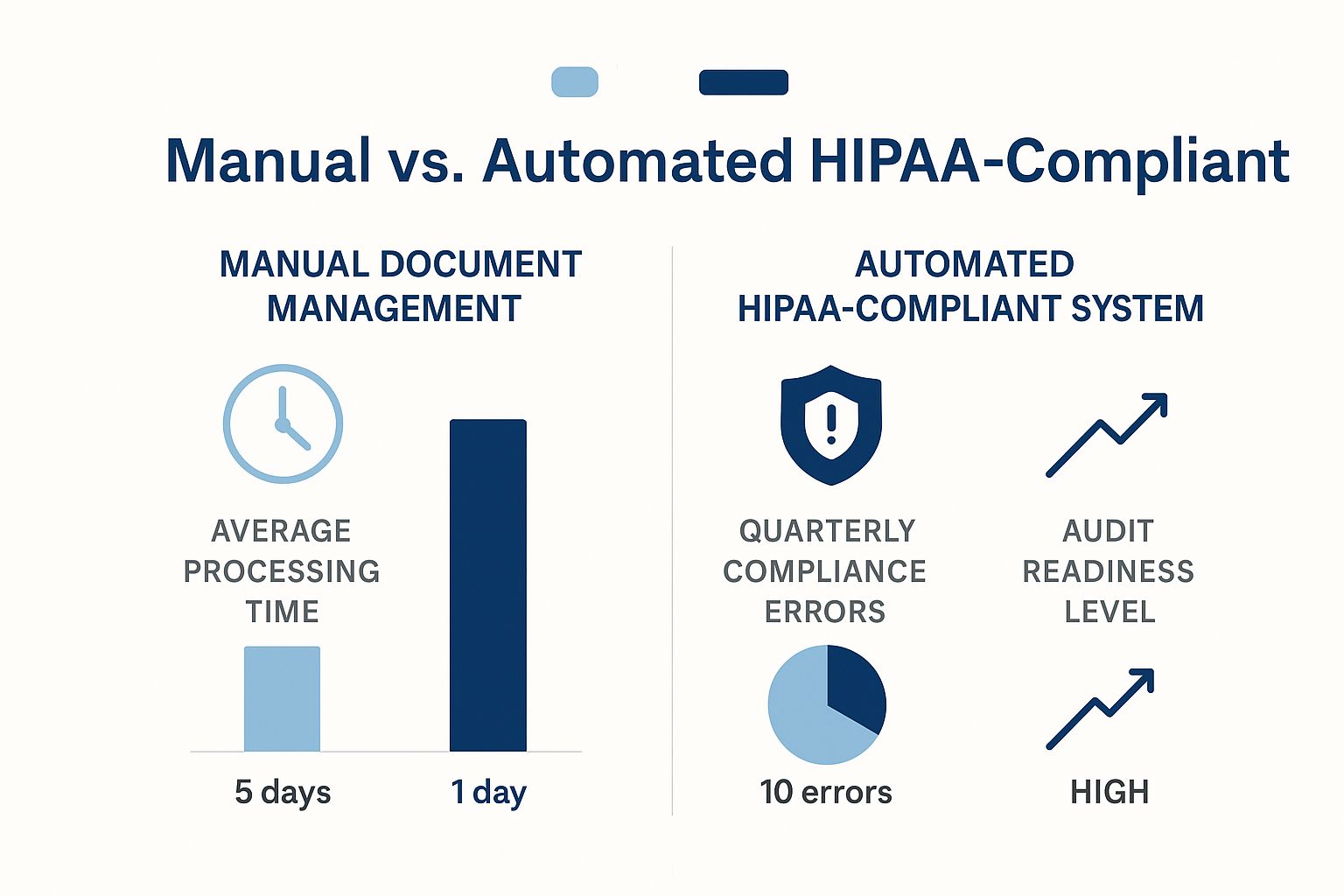
The numbers speak for themselves. An automated system doesn't just speed things up; it virtually eliminates compliance errors. That kind of improvement makes you far more confident and prepared if an auditor ever comes knocking.
Plan Your Data Migration Strategy
Once you know where your risks are, the next big step is figuring out how to get all your existing PHI into the new system. This is a delicate operation that requires real precision. You can't just drag and drop a few folders and hope for the best. A phased, controlled approach is essential to make sure no data gets lost, corrupted, or accidentally exposed during the move.
Your migration plan should be detailed and cover:
- Data Cleansing: Before you move anything, take the time to identify and either archive or securely destroy documents that are outdated, duplicated, or no longer needed.
- Validation: Set up a clear process to check and double-check that every piece of data has been transferred accurately and completely.
- Timing: Plan the migration for a weekend or after hours to cause as little disruption as possible to your team’s daily work.
A well-planned migration protects the integrity and availability of PHI from the moment it lands in the new system. If you rush this part, you can create data loss and compliance holes that are a nightmare to fix later on.
When considering a DMS, a fundamental choice is whether to host it yourself (on-premise) or use a cloud provider. Each has significant implications for cost, security, and maintenance in a HIPAA context.
Here's a look at how they stack up.
On-Premise vs Cloud HIPAA DMS A Comparison
| Factor | On-Premise System | Cloud-Based System |
|---|---|---|
| Initial Cost | High upfront investment in hardware, software licenses, and infrastructure. | Lower upfront cost, typically a predictable monthly or annual subscription fee. |
| Control & Customization | Complete control over hardware, software, and security configurations. | Less direct control; you rely on the vendor's infrastructure and security measures. |
| Maintenance | Your internal IT team is responsible for all updates, patches, and maintenance. | The vendor handles all maintenance, security updates, and infrastructure management. |
| Security Responsibility | You are solely responsible for physical security, data backups, and disaster recovery. | Security is a shared responsibility. The vendor secures the cloud, you secure access. |
| Scalability | Scaling requires purchasing and installing new hardware, which can be slow and costly. | Easily scalable. You can adjust storage and user counts as your needs change. |
| Accessibility | Access is typically limited to your internal network unless you configure secure remote access. | Accessible from anywhere with an internet connection, protected by secure logins. |
Choosing between on-premise and the cloud depends heavily on your organization's resources, IT expertise, and risk tolerance. While on-premise offers maximum control, the cloud provides scalability and shifts the heavy lifting of maintenance to the vendor, which is why many organizations find it a more practical fit.
Configure User Roles and Train Your Staff
With your data securely in its new home, the focus turns to the people who will be in the system every day. This is where you bring HIPAA's "minimum necessary" principle to life by carefully setting up user roles and permissions.
You'll need to configure access levels within the HIPAA compliant document management system based on specific job functions. A nurse practitioner needs access to different records than a front-desk administrator, who in turn needs different permissions than a third-party billing contractor. The rule is simple: each role should only grant access to the absolute minimum amount of PHI needed for that person to perform their duties.
After the roles are set, comprehensive training is absolutely mandatory. Your team needs to understand more than just how to use the software; they need to understand why all the security rules and protocols are in place. This training needs to be documented and should become a standard part of the onboarding process for every new hire. At the end of the day, a secure system is only as strong as the people who use it.
Maintaining Ongoing HIPAA Compliance

Getting HIPAA compliant isn't a destination you arrive at. It's not a project you finish and file away. Think of it more like maintaining a high-performance vehicle; you don't just buy it and assume it will run perfectly forever. It needs regular oil changes, tire rotations, and system checks to stay safe and reliable on the road.
Your commitment to protecting PHI is the same. It requires constant attention and adaptation to keep up with new threats and evolving rules. A hipaa compliant document management system is a critical part of your toolkit, but you only unlock its full value when you build strong, consistent practices around it. This is about shifting from a "set it and forget it" mentality to a proactive culture where security is second nature.
Establish a Cadence of Regular Audits
The bedrock of any long-term compliance strategy is a routine of regular check-ups. You can’t defend against vulnerabilities you don't know exist. This makes periodic risk analyses and access log audits absolutely essential. Think of these as your security team's regular patrol, allowing you to spot suspicious activity before it escalates into a major incident.
Get these activities on the calendar and treat them as unbreakable appointments:
- Quarterly Access Log Reviews: Every three months, set aside time to comb through the audit trails in your document management system. You’re looking for red flags like after-hours logins from typically 9-to-5 employees, unusually large file downloads, or a string of failed login attempts that might indicate a brute-force attack.
- Annual Risk Analysis: At least once a year, perform a top-to-bottom risk analysis. This isn't just a repeat of your initial assessment. It’s a chance to identify new weak spots that have appeared because of new software, different workflows, or staffing changes.
This rhythm of oversight is fundamental to staying compliant and proves you’re serious about security if an auditor ever comes knocking. For those using cloud services, tools for Cloud Security Posture Management (CSPM) can be a game-changer, helping to automatically find and fix configuration errors that could leave you exposed.
Evolve Your Policies and Training
The worlds of healthcare and technology never stand still. New regulations appear, and cybercriminals are always inventing new ways to attack. Your security policies can't be carved in stone; they need to be living documents that you update as the landscape changes. When a new rule is passed or you bring a new technology on board, your internal policies should be updated right away, and those changes must be clearly communicated to your entire team.
That brings us to the most crucial element of ongoing compliance: your people.
Technology provides the tools for security, but a vigilant, well-trained team builds the culture. Continuous employee training transforms your staff from a potential vulnerability into your greatest security asset.
Regular, bite-sized training keeps security practices front and center. Instead of one long, boring annual session, try short monthly refreshers on specific topics like spotting a sophisticated phishing email, securely sharing documents with outside partners, or why password complexity matters. This security-first mindset is foundational, and you can dig deeper by reading our guide on document management best practices.
The urgency for these systems is clear, with the market projected to grow from USD 5.31 billion in 2025 to USD 8.94 billion by 2033. AI is now playing a bigger role, adding smarter features to help manage and protect PHI more effectively.
Answering Your Top HIPAA DMS Questions
Diving into the world of HIPAA compliance can feel like navigating a minefield, especially when you’re choosing something as fundamental as a document management system. The stakes couldn't be higher, and getting it right is crucial for keeping patient data safe and your operations running smoothly.
Let’s cut through the noise. Below, we’ve tackled some of the most common questions we hear from healthcare professionals just like you. Our goal is to give you clear, straightforward answers to help you make confident decisions.
Can I Use Google Drive or Dropbox for HIPAA Compliance?
This is easily the most frequent question we get, and the answer isn’t a simple yes or no. The free, standard versions of cloud storage like Google Drive or Dropbox are absolutely not HIPAA compliant. They don't have the necessary security architecture, and crucially, they don't come with a Business Associate Agreement (BAA).
However, their paid, business-focused versions—think Google Workspace or Dropbox Business—can be made compliant. But it’s not automatic. You have to sign a BAA with them, and then it's on you to meticulously configure every single security setting. Just paying for the subscription does nothing; you are still responsible for locking down permissions, access controls, and workflows to meet HIPAA standards.
This is why many organizations find that a dedicated hipaa compliant document management system is a much more direct and secure route, as it's built from the ground up with these protections baked in.
What Is a Business Associate Agreement and Why Is It Essential?
Think of a Business Associate Agreement (BAA) as a legally binding contract between you (the "covered entity") and any vendor that handles your patient data (the "business associate"), like a DMS provider. This document isn't just a piece of administrative paper; it's a cornerstone of HIPAA.
The BAA legally obligates the vendor to protect your Protected Health Information (PHI) with the same rigor you do. It outlines exactly how they'll secure the data, report any breaches, and what safeguards they have in place.
Sharing PHI with any vendor without a signed BAA is a direct HIPAA violation. It is the single most important document for establishing a compliant relationship with any third party that touches patient data. Never, ever move forward without one.
Does Using a Compliant DMS Make Us Automatically Compliant?
No, and this is a dangerous misconception. Investing in a HIPAA-compliant DMS is a fantastic and necessary step, but it doesn't magically grant your entire organization "instant" compliance.
Think of it as a shared responsibility. The DMS provider handles the security of the platform's infrastructure—the servers, the network, the core software. But you are responsible for how your team uses that platform.
This means you still own critical ongoing tasks, such as:
- Setting up user roles and access levels to enforce the "minimum necessary" principle.
- Training your staff on how to handle documents securely within the system.
- Developing and enforcing your own internal privacy and security policies.
- Regularly conducting risk assessments and reviewing who is accessing what in the audit logs.
The DMS is the secure vault, but your internal processes and people are the ones who hold the keys.
What Are the Biggest Mistakes When Choosing a DMS?
When picking a system, a few common slip-ups can completely undermine your compliance efforts before you even start.
One of the biggest is just taking a vendor's "HIPAA compliant" marketing slogan at face value. You have to do your homework. Ask for the technical details. Scrutinize their BAA, verify their encryption methods (both for data at rest and in transit), and don't be afraid to ask tough questions.
Another classic mistake is focusing only on the tech and forgetting about the people. The most secure system on earth is useless if an untrained employee shares their password or clicks on a phishing link. A solid implementation plan must include thorough and continuous staff training.
Finally, don’t choose a system that’s a nightmare to use. If the software is clunky and confusing, your team will find workarounds. They'll start emailing files or using personal cloud accounts, which completely defeats the purpose of your investment. Usability is security. The easier it is to do the right thing, the more likely your staff will do it, especially for routine tasks like the ones detailed in our guide on HIPAA compliant document sharing.
Ready to simplify your document workflows without compromising on security? Whisperit provides an advanced AI-powered platform designed with privacy at its core, hosted securely in Switzerland and compliant with GDPR and SOC 2 standards. Transform how you create and manage documents. Explore Whisperit today.